How to use innerHTML in React?
In the intricate and dynamic world of web development, React stands out as a powerful library, offering a robust set of tools for building interactive and efficient user interfaces. Among its various features, dangerouslySetInnerHTML presents itself as a double-edged sword. It provides developers with the capability to directly insert raw HTML into React components, unlocking a realm of possibilities for content rendering and user interaction. However, this power comes with its own set of complexities and potential pitfalls, especially in terms of security. The potential for cross-site scripting (XSS) attacks and the injection of malicious code make it a feature that must be handled with utmost care. In this comprehensive guide, we delve deep into the intricacies of dangerouslySetInnerHTML, exploring its uses, inherent risks, and the best practices for safe implementation. Whether you’re a seasoned developer or just starting out with React, this guide aims to equip you with the knowledge and tools needed to navigate this challenging aspect of web development securely and confidently.
What is React dangerouslySetInnerHTML?
In the realm of React, a JavaScript library renowned for creating user interfaces, dangerouslySetInnerHTML emerges as a unique attribute, designed to integrate raw HTML into the Virtual DOM. This attribute is the React-equivalent of innerHTML used in traditional browser DOM manipulation. However, it’s crucial to approach its usage with caution due to the potential risks associated with cross-site scripting (XSS) attacks.
Why dangerouslySetInnerHTML is Necessary?
React champions the synchronization between the Virtual DOM and the actual browser DOM, promoting efficient updates and rendering. Typically, direct manipulation of the DOM is discouraged to maintain this harmony. However, there are instances where rendering HTML content, originating from user-generated sources like comments or blog posts, becomes imperative. dangerouslySetInnerHTML steps in as React’s solution to this, albeit with a clear warning embedded in its name. Also, discover how Codelyzer revolutionizes code analysis – your key to cleaner, more efficient programming.
Key Characteristics and Usage
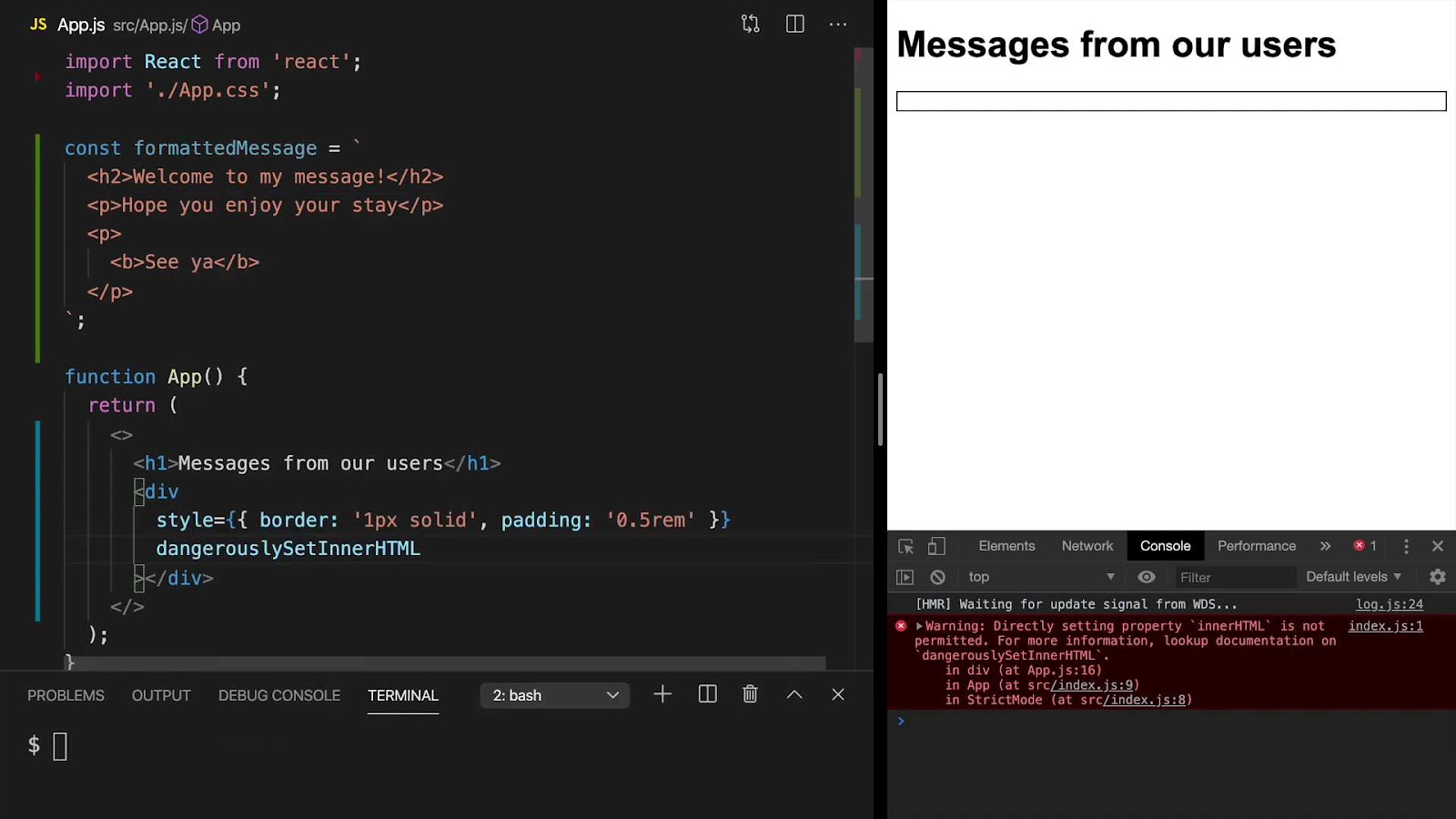
Unlike innerHTML, dangerouslySetInnerHTML does not provide the ability to retrieve data. Its sole purpose is to enable the passing of HTML markup to be rendered. Here’s a breakdown of its implementation:
- Passing the HTML String: To inject HTML content, one must encapsulate the HTML string within an object, assigning it to the __html key;
- Implementation in a React Component: Below is a detailed example showcasing how to utilize dangerouslySetInnerHTML within a React component;
- javascript
export function EnhancedComponent() {
const boldText = "<b>Welcome</b>";
return <div dangerouslySetInnerHTML={{ __html: boldText }} />;
}In this example, the output will visibly render “Welcome” in bold, rather than displaying the raw HTML tags.
Best Practices and Safety Precautions
Given its potential security implications, it’s paramount to use dangerouslySetInnerHTML judiciously. Below are some recommended practices and safety tips:
- Sanitize HTML Content: Always sanitize user-provided HTML content to prevent XSS attacks. Libraries such as DOMPurify can assist in cleaning up the HTML;
- Limit Usage: Restrict the use of dangerouslySetInnerHTML to scenarios where it’s absolutely necessary. Explore alternative solutions when possible;
- Ensure Content Source Trustworthiness: Be certain that any HTML content passed to dangerouslySetInnerHTML originates from a reliable source.
The Risks of Using dangerouslySetInnerHTML in React
The attribute dangerouslySetInnerHTML holds significant power in the React framework, enabling developers to embed raw HTML directly into components. Despite its capabilities, this feature carries substantial security risks, particularly when user-generated content is involved.
The Potential for Malicious Content
Consider a scenario where a website incorporates a section for user comments, complete with a rich text editor that facilitates the entry of HTML-styled text. This seemingly harmless feature could potentially become a gateway for malicious actors to inject harmful scripts, thereby compromising the security and integrity of the site and its visitors.
Embedding Scripts: While the HTML5 specification has measures to block the execution of <script> tags inserted via dangerouslySetInnerHTML or innerHTML, cunning users might still exploit other avenues. For example, scripts can be embedded as event handler attributes within HTML tags:
const maliciousImage = "<img src='1' onerror='alert(\"Error loading image\")'>";
const nameField = "<b onmouseover='alert(\"mouseover\");'>Mike</b>";In these instances, the script within the onerror or onmouseover attributes would execute, potentially leading to undesired outcomes.
Safeguarding Content with HTML Sanitization
Thankfully, there are tools designed to counteract these threats by sanitizing HTML content, stripping away any hazardous elements or attributes. Among these, DOMPurify stands out as a widely recognized and trusted HTML sanitizer. It meticulously scans the HTML code, excising any segments that may pose security risks.
Utilizing DOMPurify: To employ DOMPurify in safeguarding a React component, one would follow these steps:
import DOMPurify from 'dompurify';
export function SecureComponent() {
const userContent = "<img src='1' onerror='alert(\"Error loading image\")'>";
// Sanitize the user-provided HTML content
const cleanContent = DOMPurify.sanitize(userContent);
// Safely embed the sanitized content into the component
return <div dangerouslySetInnerHTML={{ __html: cleanContent }} />;
}In this example, DOMPurify ensures that any malicious scripts or attributes are removed, rendering the content safe for rendering.
Proactive Measures and Recommendations
To maximize security and minimize risks associated with dangerouslySetInnerHTML, developers are encouraged to:
- Regularly Update Sanitization Libraries: Ensure that tools like DOMPurify are consistently updated to leverage the latest security enhancements;
- Restrict Usage: Limit the use of dangerouslySetInnerHTML to scenarios where it is absolutely necessary, exploring safer alternatives whenever possible;
- Educate and Train Development Teams: Ensure that all team members are aware of the potential risks and best practices associated with embedding raw HTML.
By adopting these practices, developers can strike a balance between functionality and security, ensuring a safer experience for both users and developers alike.
Conclusion
As we wrap up this extensive exploration of React’s dangerouslySetInnerHTML, it is evident that while this feature offers a powerful means for HTML content integration, it necessitates a vigilant and cautious approach. The capability to embed raw HTML directly into React components can enhance content dynamism and user interaction, but it also opens the door to potential security vulnerabilities, especially when handling user-generated content.
In conclusion, while dangerouslySetInnerHTML presents certain challenges and risks, a comprehensive understanding, coupled with rigorous content sanitization and mindful implementation, can lead to safe and effective usage. Developers are entrusted with the responsibility of balancing functionality and security, ensuring that the power of React is harnessed to create not just dynamic and interactive, but also secure and trustworthy web applications.